Setting the SameSite header for Kentico cookies
SameSite is an HTTP cookie header that provides a certain level of protection against Cross-site request forgery (CSRF) attacks by limiting where and how the cookies can be used. This article describes two methods of setting this header in Kentico.
The SameSite header can have 3 possible values:
- None – means no restrictions. The cookie can be sent to any third-party site on any cross-site request. This value requires that the Secure header is set as well.
- Lax – means that the cookie will only be sent on same-site requests or through top-level navigation to another site (excluding loading images and resources from other sites).
- Strict – means that the browser will refuse to send the the cookie on any cross-site request.
Until recently, browsers treated all cookies without this attribute as SameSite=None. This means that there were no restrictions. New versions of modern browsers will now consider these cookies as SameSite=Lax. For example, Chrome already announced this change starting Chrome version 80.
As a best practice (and to aviod warnings in the browser console), it’s recommended to explicitly specify the SameSite header for all cookies. So, how can this be done in Kentico?
Both of the below methods will work for MVC and Portal Engine projects. When using MVC, make sure you perform these steps on both the MVC project and the Administration project.
Method 1: Modifying the httpCookies element in the web.config file (Kentico 12 only)
The easiest way to modify HTTP cookie headers is to specify the SameSite attribute in the web.config file of the website or web application. Since this method requires .NET Framework 4.7.2 or .NET Framework 4.8, it will only work for Kentico 12 as older versions of Kentico don’t support these frameworks. If your Kentico 12 instance targets a lower version of .NET, you will need to change the target framework first.
The following example will set the SameSite header to Lax and will also set the Secure header, meaning the cookie will only be delivered if the connection is secure (i.e. HTTPS with a valid certificate):
<configuration>
<system.web>
<httpCookies sameSite="Lax" requireSSL="true" />
<system.web>
<configuration>
You can read more about this method in Microsoft's official documentation.
Method 2: Using IIS Rewrite rules (all Kentico versions)
This method will rewrite all HTTP headers while adding the SameSite and Secure headers to all cookies. First, you will need to download and install the IIS Rewrite module.
After you installed the module, you can add the following rewrite rule to your web.config file to set the SameSite header to Lax and to add the Secure header:
<rewrite>
<outboundRules>
<rule name="AddSameSitecookie" enabled="true" patternSyntax="ECMAScript">
<match serverVariable="RESPONSE_Set-Cookie" pattern="(.*)=(.*)$" negate="false" />
<action type="Rewrite" value="{R:0}; SameSite=Lax; Secure" />
</rule>
</outboundRules>
</rewrite>
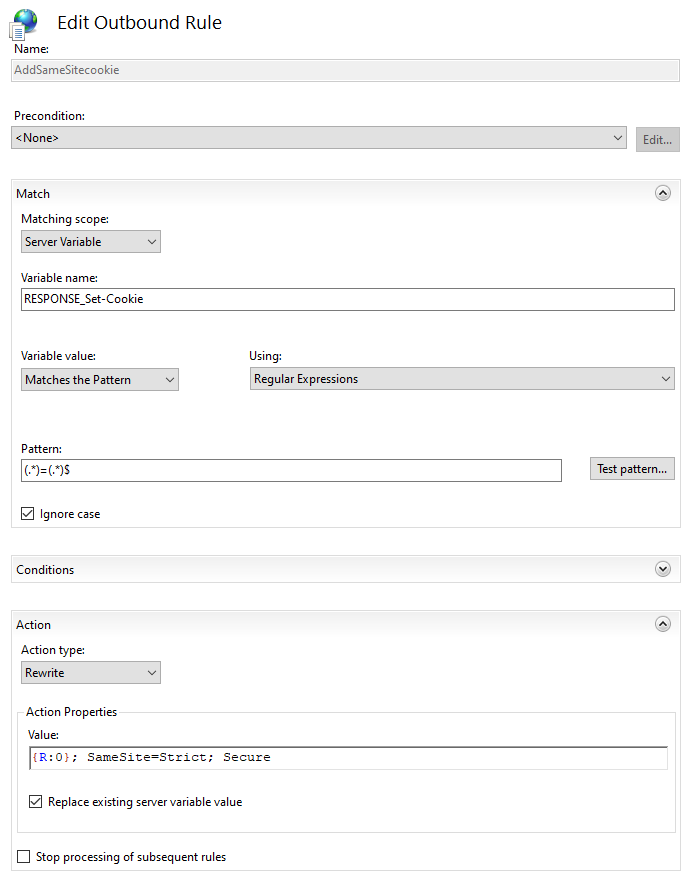
Alternatively, you can create the rule in IIS Manager:
- Open IIS Manager
- Select your website in the left navigation
- Open the URL Rewrite module
- Click on Add Rule(s)… and select Outbound rules > Blank rule
- Configure the rewrite rule like this:
- Name: AddSameSiteHeader
- Precondition: <None>
- Matching scope: Server Variable
- Variable name: RESPONSE_Set-Cookie
- Variable value: Matches the Pattern
- Using: Regular Expressions
- Pattern: (.*)=(.*)$
- Ignore case: YES
- Action type: Rewrite
- Action Properties > Value: {R:0}; SameSite=Lax; Secure
- Replace existing server variable value: YES
- Stop processing of subsequent rules: NO
- Click on Apply
Summary
Whether you choose any of the two methods described in this article to set the SameSite header of your cookies, you will also need to decide which value you will be using for this header. Most sites will work fine with the Lax setting, but before you make that decision, you may want to read an in-depth explanation of how it all works.