Hello Bryan,
thank you for the response!
Based on your suggestion I added your snippet
<configuration>
<configSections></configSections>
.
.
<system.webServer>
<httpProtocol>
<customHeaders>
<add name="X-Frame-Options" value="ALLOW-FROM http://xxx.xx" />
</customHeaders>
</httpProtocol>
</system.webServer>
.
.
</configuration>
and tested it by trying to load the website into an iframe using the IE 11. Unfortunately the X-Frame-option stays at "SAMEORIGIN" and therefore i'm not able to get the page loaded.
What i'm missing here?
Update - Solution
After some hours i found the solution.
By default Kentico sets the x-frame-options to "SAMEORIGIN" to prevent "Clickjacking". You can finde the documentation here.
To add the code snippet above as mentioned by Bryan and here is just the halfe way.
You also have to remove the "SAMEORIGIN" setting from the header. You could to this by simply follow the steps in the documentation (linked above).
If you don't remove the prior set "SAMEORIGIN" setting you will get a result like this:
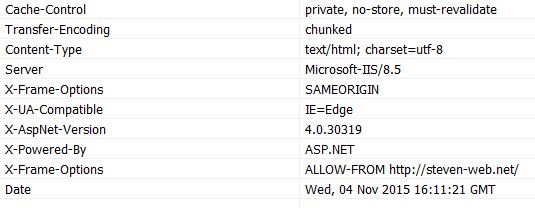
As shown in the picture - the x-frame-option is declaried two times. To slove this just add
<add key="CMSXFrameOptionsExcluded" value="/" />
to you web.config.
Regards Stefan