Page macro expressions security
The macro engine is a powerful option you can use when developing your web project. Page macros are just one part of this engine. Since changes have been made to the page macro’s security in hotfix 8.1.11, this article will primarily focus on page macro expressions and the appropriate security check you should be aware of.
How are macro expressions secured?
First, let me explain how the macro expressions, in general, are protected. When a user saves a macro expression, the system adds a security signature. The security signature contains:
-
The user name of the person who saves the macro
-
The hash computed from the given expression
Imagine that we’d like to use macros to get information about a user. In this case, we will try and find out about a user named Andy. Let’s say we need to find out whether or not Andy is a Global Administrator. The following macro will come back as
true if Andy is a Global Administrator, otherwise it will come back as
false.

The system resolves the macro only if the
user specified by the signature has permission to do so – this requires read permission for module Users. So if the macro was
signed by a user who has Read permission for module Users, this macro will be resolved for all users who access the page where the macro is placed. Everyone can see if Andy is the Global Administrator or not since the macro was signed by a user with the necessary permissions.
What happens if the mentioned macro is
signed by a user who doesn’t have Read permission for module Users? The answer is
nothing – the macro expression will not be resolved. This means that nobody except for the user who signed the macro will see if Andy is the Global Administrator or not. This is how macros are secured – the user who signs the macro must have permission to access the object.
Page macro expressions
Up until the 8.1.11 hotfix – the hotfix released on November 7, 2014 – the security check in the page macro was evaluated in a different way. In order to protect page content, the page macro was resolved in the context of the current user, not in the context of the user who signed the macro. The main idea here was to filter the TreeNodeCollection class to get only pages that the current user is able to read.
Example:
Andy adds the following macro expression to the page:
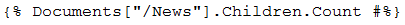 What is the macro expression result?
What is the macro expression result?
It will return the number of the child pages located under the “/News” page.
When is the macro expression resolved?
When the current user who visits the page the macro expression is placed on has permission to read the child pages located under the “News” page. It doesn’t matter if Andy (user who signed the macro) has the appropriate permissions for these pages or not. That’s the difference.
When is the macro expression not resolved?
When the current user doesn’t have the appropriate permission to read the child pages located under the “/News” page. Again, it doesn’t matter if the user who signed the macro has the appropriate permission or not.
What has been changed in hotfix 8.1.11?
We were aware of the inconsistency created by evaluating macro expressions, so we’ve decided to unify the page macro expression permission check with the rest of the system. Your great feedback has assured us that this is the right way to go. If you apply hotfix 8.1.11 you can work with page macros in the following ways:
I. Securing page macro expressions against the user who signed the macro
This will be the default scenario after applying the hotfix 8.1.11. It will make your work much easier since you can work with page macros in the same way as you would with the other types of macros.
Example:
The macro expression:
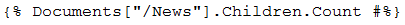
will be resolved when the user who signed it has the necessary page permission. If this requirement is met, all the users who visit the page where the macro is placed will see the number of child pages located under the “/News” page. As you can see, the same security mechanism also works for other macro types.
II. Securing page macro expressions against the current user
If you decide to evaluate the page macro security check against the current user, you can use the
WithPermissionsCheck property of the TreeNodeCollection class. This property has the same effect as the “Check permission” property of the viewer web parts like Repeater, etc. With this property you can achieve the same behavior as it was before applying hotfix 8.1.11.
Example:
The macro expression:
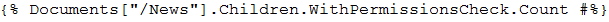
will be resolved when the current user who visits the page where the macro is placed has permission to read the child pages located under the “/News” page.
Summary
Let’s sum up how the page macro security works and what the security check options are after applying hotfix 8.1.11.
Before applying hotfix 8.1.11
-
The security check for the page macro is evaluated against the current user, not the user who signed the macro.
-
You can use the web.config key – CMSCheckPermissionsForDocumentCollection (true/false) – to disable the security check. In that case, you have to take into account that this can lead to potential security issues. Users who don’t have the permission to view specific page data will be able to access it.
After applying hotfix 8.1.11:
-
The security check for the page macro is evaluated against the user who signed the macro.
-
You also have the option to force the evaluating security check against the current user with the following macro parameter: WithPermissionsCheck.
I hope that the information presented above will help you use and secure your page macro expressions. Thanks for stopping by. Please feel free to leave your questions, comments and feedback below.