Macros |
|
|

|
|
|
Macros |
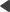
|
|

|
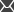
|
|
|
||
Whenever a user saves a macro expression, the system automatically adds a security signature. This signature contains the user name of the macro's author and a hash of the expression. If the execution of the macro requires any permissions (e.g. to read data from a specific object collection), the system resolves the macro only if the user specified by the signature has the appropriate permissions.
To improve security, the hash function used when creating macro signatures appends a salt to the input (a sequence of additional characters). By default, the system uses the application's main database connection string as the salt (i.e. the exact CMSConnectionString value set in the web.config file). You can also assign a custom salt through the CMSHashStringSalt web.config key.
If your application's salt changes, the security signatures of existing macro expressions become invalid. This may lead to problems with unresolved macros in certain scenarios, for example when:
•The connection string of your application has changed, e.g., when moving to a different server or after setting a new database password.
•You are using Content staging to transfer data containing macros to an instance of Kentico CMS with a different connection string.
•You have set a new custom salt via the CMSHashStringSalt web.config key.
This page allows you to fix invalid macro signatures by re-signing all macros using a new hash salt:
1. Fill in the Old salt field.
•If you leave the Sign all macros option disabled, the system attempts to re-sign macros based on the data in the original signatures. As a result, only macros that have a valid signature under the old salt are re-signed and the user names of the macro authors remain unchanged. You need to enter the old salt that was used to generate the security hash of the existing macro expressions in the system.
oBy default, the old salt is the value of the application's previous connection string in format:
Persist Security Info=False;database=DBName;server=ServerName;user id=DBUser;password=pwd;Current Language=English;Connection Timeout=240;
oIf your application uses a custom hash salt, enter the original value of the CMSHashStringSalt web.config key.
•If you enable Sign all macros, the macro re-signing process skips the signature integrity check and creates new signatures for all macros. This includes macros that are unsigned or have invalid signatures. The new signatures use the name of the user who started the re-signing procedure. You do not need to enter the old salt value in this case.
2. Type in the New salt that will be used to re-sign the macros.
oBy default, the field automatically loads the current application's hash salt value. To enter a different value, disable the Use current salt option.
|
Important!
In order for the system to correctly validate macro signatures, the new hash salt value must match the current salt of the application (the connection string or CMSHashStringSalt key value).
Only set a different value than the current salt if you are planning to change the connection string or custom salt.
|
3. Click Update macro signatures.
The system replaces the security signature in all occurrences of macros based on the new salt.
Additional resources:
•Developer's Guide -> Development -> Macro expressions
•Developer's Guide -> Development -> Macro expressions -> Security